SonarQube plugin for Mule 4.x projects
Introduction
MCR Sonar plugin is a Sonarqube plugin for analysis of Mule 4.x projects or files. The plugin analyses Mule 4.x code base and calculates various metrics and checks the code for any code violations based on Mule4 Code Reviewer code violation rules. The Sonar plugin calls the Mule4 Code Reviewer command line or the Enterprise Cloud instance behind the scenes for static code analysis.
As part of continuous integration in a CI-CD cycle, a static code analysis is typically initiated at the end of Jenkins or Hudson build job. Sonarqube uses a relational database to store the results of static analysis and has a great GUI to display the results. Sonarqube supports multiple databases like Oracle, SQL Server, MySQL, PostgreSQL etc.
Sonarqube stores a snapshot of each analysis performed in its repository and thus provides opportunity to monitor the trends in code quality over a period of time. To ensure optimal code quality of your Mule 4.x projects and files, use our Sonarqube plugin. You can Contact us to set up a demo of the plugin and enquire about pricing
Features
Key Features
- Multiple Deployment Models: Mule4 Code Reviewer (M4CR) plugin for SonarQube can be deployed on any OS (Windows, Linux, Solaris etc.) or any IaaS platform (AWS, Azure etc.) that can run Java similar to SonarQube.
- Support for Multiple Projects: M4CR plugin for SonarQube provides support for scanning source code of single or multiple projects. You can run analysis from the Mule4 source code repository that has multiple projects. M4CR plugin for SonarQube works with Mule Code Reviewer to identify all the projects and lists the issues and recommendations for all the resources of all the projects.
- Project and Rule Metrics: It provides support for summary metrics of project that includes number of process definitions, connection resources, activities, transitions and mappings under General section of Metrics tab
- CWE classification: M4CR plugin for SonarQube categorizes the issues with CWE (Common Weakness Enumeration) classification where applicable and adds the tags. You can filter the issues using cwe tag under the Issues section to find the associated vulnerabilities, bugs and code smells.
- Issue Details: M4CR plugin for SonarQube provides visibility to drill down to process, activity and configuration level details or the transition paths in source code that failed the rules in the Issues section. For global variables, it provides a list of Global variables that failed code review rules
- Customization: M4CR plugin for SonarQube provides a platform for rules customization as per your best practices. User can provide a rules override file in the sonar-project.properties file or in the Administration tab that can be used to update the severity, description and to filter certain processes or connections from being scanned.
Installation
Sonar plugin for Mule 4.x Installation
- Install the SonarQube server (6.7.x LTS version or later) if you have not already done so. Please refer to the latest version of SonarQube installation guide
- Download the M4CR plugin for SonarQube file (.tar.gz for linux and .zip for Windows) from the download portal provided as part of your Enterprise license
- Untar or unzip the downloaded file to a directory on the system. The unzipped version has a jar file named sonar-ccl-tib-M4CR-plugin-
.jar. - Copy this jar file to SonarQube installation at SONARQUBE_HOME/extensions/plugins. Make sure you delete any existing Mule4 plugins from your installation before copying the jar file
- Restart SonarQube server
Mule 4.x Sonarqube plugin Configuration
Global Configuration
M4CR plugin for SonarQube can be configured globally for applying the settings across all the projects
- Login as a SonarQube administrator to change global configuration
- Go to Administration > Configuration > General Settings. You should see CCL M4CR Sonar plugin on the left hand side as shown in the image below. This shows successful installation of the plugin
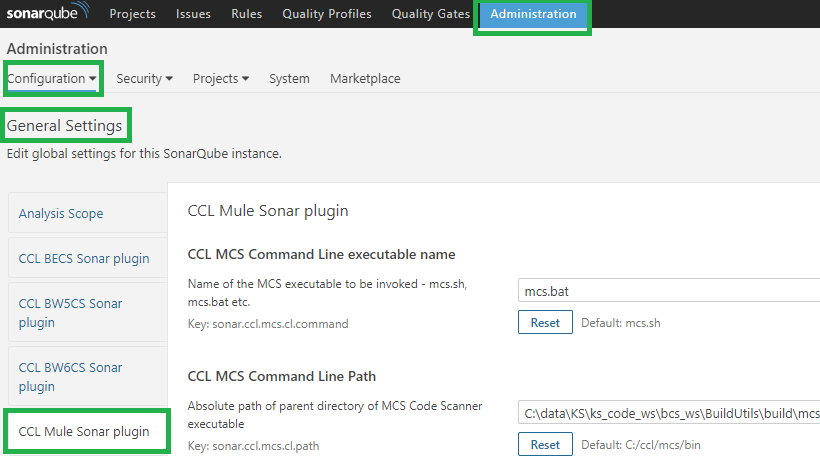
- Configure the values for CCL M4CR Command Line executable name (mcs.bat for Windows and mcs.sh for Linux) as shown in image below
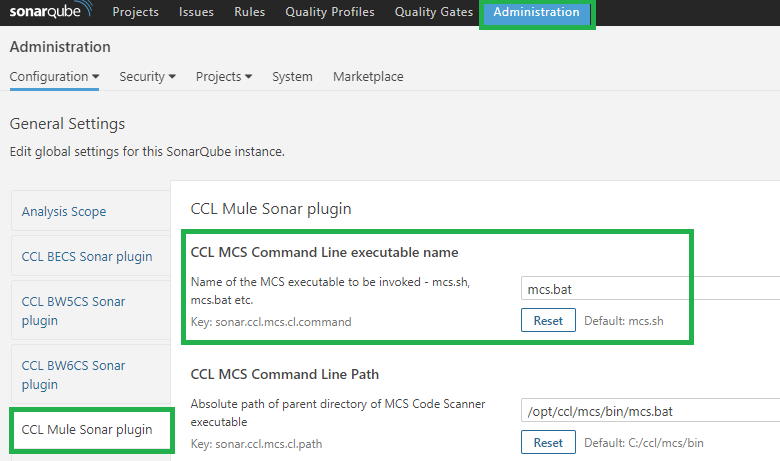
- Similarly, configure the CCL M4CR Command Line path. This is the location (full absolute path) of the M4CR installation location where the executable is available
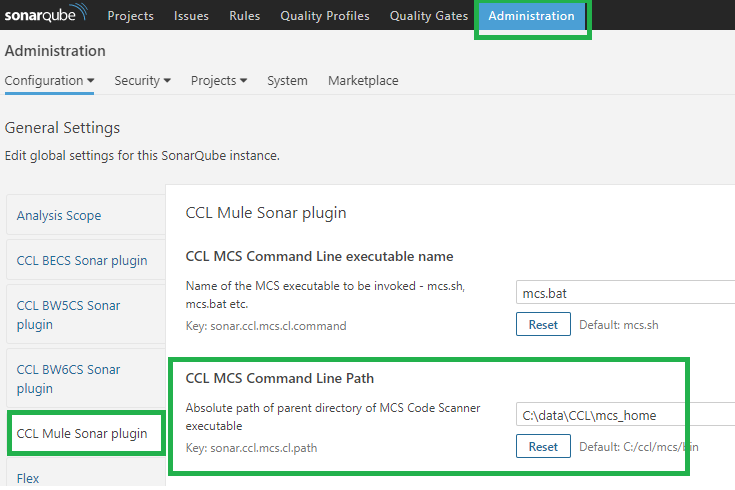
- If you are using an older version of SonarQube than 6.7.1, or when using custom Quality profiles, make sure that the rules with naming convention CCL M4CR* are activated
Project Configuration
Settings for M4CR plugin for SonarQube can be configured at a Project level in the SonarQube GUI. Note the Mule4 Code Reviewer executable and the path needs to be configured in Global Configuration as noted above. At project level, you can configure the project level rules override settings.
- Go to Projects >
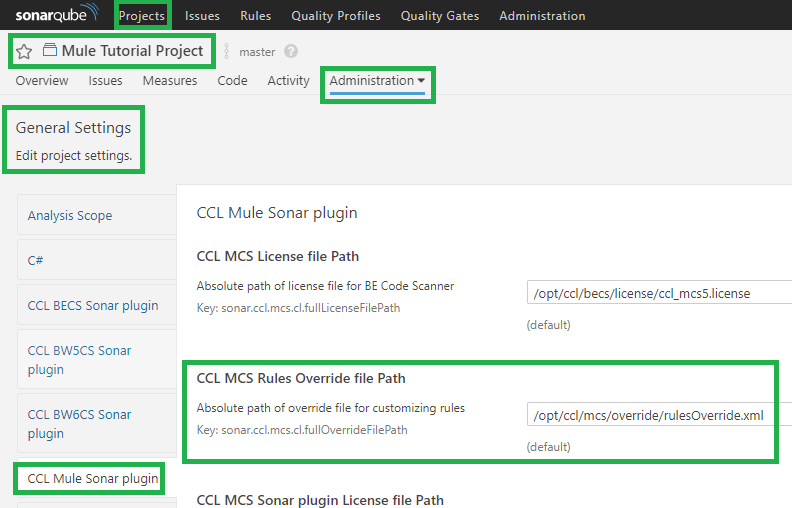
> Administration > General Settings. You should see CCL Mule Sonar plugin on the left hand side as shown in the image below. 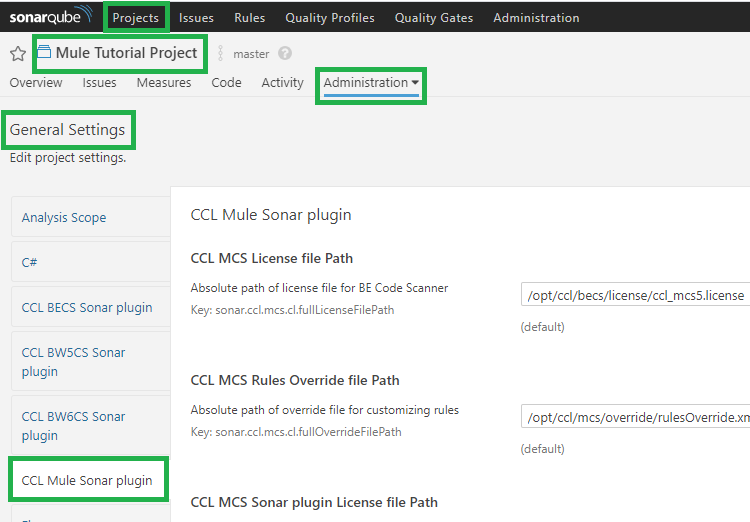
- You can also configure the rules override file for the project. This overrides the default override file specified in Global Configuration section. If a value is provided in the sonar-project.properties file, then that value overrides this value.
Running Analysis
SonarQube provides various options to run the analysis on a project. You can find the details of different types of Analyzers in SonarQube documentation. M4CR plugin for SonarQube has been tested to run using Sonar-runner, Ant, Maven and Jenkins scanners. Other scanners might also be supported as the scanner relies only on proper plugin installation.
Setting up sonar-project.properties
# must be unique in a given SonarQube instance
sonar.projectKey=mule# this is the name and version displayed in the SonarQube UI. Was mandatory prior to SonarQube 6.1.
sonar.projectName=Mule Sample Projectsonar.projectVersion=1.0
# This property is optional if sonar.modules is set.
sonar.sources=.sonar.language=cclmule
# Encoding of the source code. Default is default system encoding
sonar.sourceEncoding=UTF-8# CCL Mule 4 Plugin options
#Rules override file path. This overrides the default value set on SonarQube Administration GUI
sonar.ccl.m4cr.cl.fullOverrideFilePath = /opt/ccl/rulesOverride.xmlDetails on different analysis parameters are provided in the SonarQube documentation - Analysis Parameters. For example, if the SonarQube server is not running on the same server where the Mule 4 project is located, you will need to add the property sonar.host.url to point to the right URL.
Properties evaluation sequence
As noted in the SonarQube documentation, in the scanner stack, properties are checked in the following order, and the first non-blank value is the one that is used.
- System property
- Scanner command-line (-Dsonar.property=foo for instance)
- Scanner tool (
of scanner for Maven for instance) - Project configuration defined in the web UI
- Global configuration defined in the web UI
- Default value
Analyzing the project
As noted above, analysis can be run using different scanners provided by SonarQube. Following steps provide details on how to run using command line SonarQube Scanner (also known as sonar-runner)
- Create the sonar-project.properties file in the project base folder containing one or more Mule 4 projects and add values for sonar.projectKey, sonar.projectName, sonar.projectVersion, sonar.sources=. and sonar.language=cclmule4. Details are provided above in sonar-project.properties section.
- Download and install sonar-runner command line version if you have not already done so.
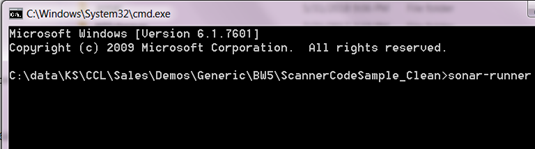
- On command line, navigate to the folder containing one or more Mule 4 projects. Make sure that sonar-project.properties file is present in this folder.
- Run sonar-runner from the project base directory.
- Once the analysis is complete, go to the Projects page on SonarQube UI and the code review snapshot from the project scan should now be available for review
Reviewing the Analysis
Note that this documentation is written using SonarQube 6.7.x LTS version. The screenshots and navigation might be slightly different based on the version you are using.
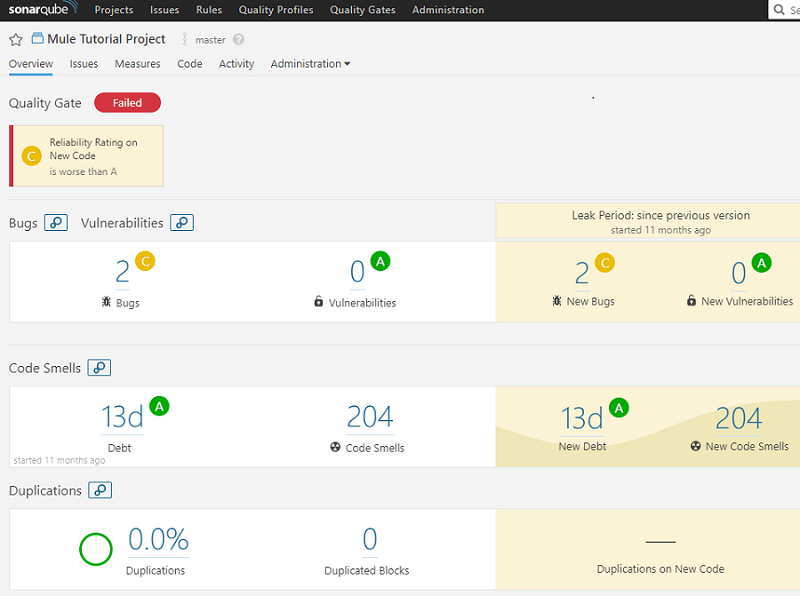
- Once the analysis is complete, you can login to the SonarQube GUI to check the project snapshot as shown in the image below.
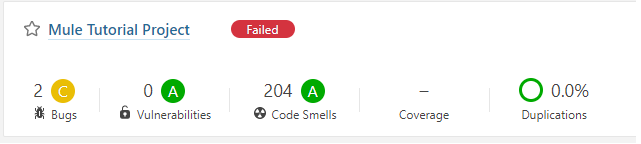
- The code violations from the Mule 4 project source code are categorized as Bugs, Vulnerabilities and Code Smells as per the SonarQube convention.
- Click on the project name to go to Project overview page
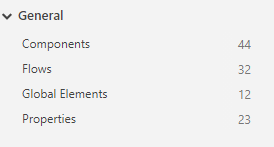
- Click on Measures tab to look at the number of Processes, Activities, Connections, Global Variables, mappings and transitions
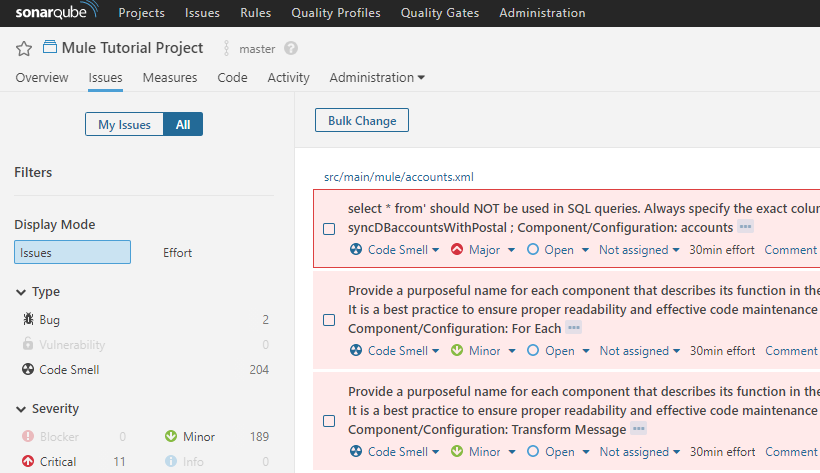
- Click on Issues tab to look at all the code violations in the project(s) scanned. As shown in the image below, each issue has a description with recommendation to fix, followed by Activity/Path where the issue occurred along with the configuration name/value where the issue occurred. If the issue has CWE classification, the associated CWE-ID is also noted in description. You can override the description found here using the rules override file
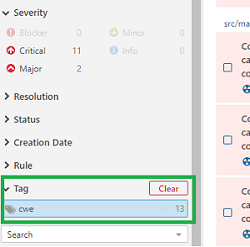
- You can toggle different criteria like Type as Bug, Vulnerability or Severity for Critical etc. to find the issues associated with them
- To find the violations which have CWE classification, you can click on Tags, click on cwe. This will bring all the violations that have an associated CWE classification.
- You can assign to a User, change the severity of an issue etc. All the standard features of SonarQube are available for the issues from Mule 4 project analysis